Hacking Humans: The Ultimate Security Weakness
Firewalls can’t stop a well-crafted lie. Social engineers don’t hack systems—they hack people. Learn how to spot manipulation, strengthen your soft skills, and turn your human firewall into the ultimate defense.

Think cybersecurity is all about firewalls and fancy encryption? Think again. The biggest vulnerability isn’t your outdated software—it’s you. Now, before you start questioning your entire existence, here’s the good news: humans may be easy to hack, but they’re also the hardest to fully compromise. Why? Because soft skills are the ultimate defense.
Let's understand how human behavior helps us level up our Governance, Risk, and Compliance (GRC) game and turn the tables on social hackers.
What Is Social Engineering?
Imagine that instead of battling firewalls and cracking code, attackers simply sweet-talk their way through your defenses. That's social engineering—the art of hacking humans instead of hardware. It's like picking a lock vs. convincing someone to hand you their keys.
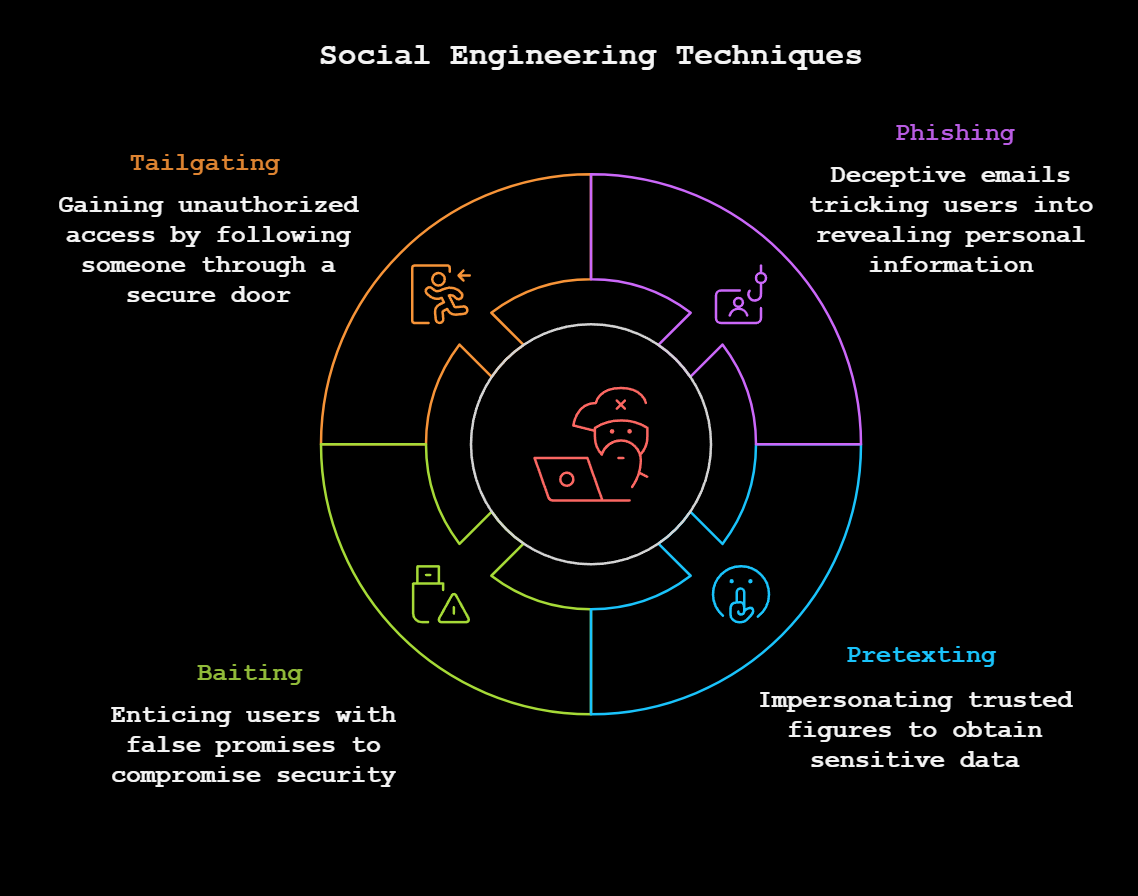
Here's some common social engineering exploits:
- Phishing: The digital equivalent of "Hey, I'm totally your bank! Confirm your password!" Complete with panic-inducing subject lines and grammar that would make your English teacher cry.
- Pretexting: When someone impersonates IT support staff to trick you into revealing sensitive information. Pro tip: Real IT professionals never call about your computer's extended warranty.
- Baiting: The classic "free candy van" of cybersecurity—except it's a mysterious USB drive labeled "Taylor Swift Unreleased Tracks 2025" Resist the urge!
- Tailgating: The "oops, forgot my badge" routine. Because why hack the door when you can just smile your way through it?
These tricks work because humans are hardwired to help and connect—which is great, until hackers exploit it like an unpatched system vulnerability.
The Human Element
Our greatest strengths—trust, curiosity, and urgency—are also our biggest weaknesses. Social engineers don't break in; they blend in. They:
- Trigger panic → "Account compromised—act NOW!"
- Tempt curiosity → "Congrats! Claim your free gift!"
- Exploit kindness → "Hey, can you hold the door please?"
Even military-grade security tools can't patch human nature. Our real power lies in sharpening our built-in security tools, the ones already configured inside our brain.
The GRC Connection
As GRC professionals, we're like risk-savvy detectives who investigate the paper trails and policy puzzles. We ask ourselves what could go wrong and how to prevent it.
By understanding how social engineers operate, we can build better defenses, train our teams to spot warning signs, and make security feel more real and relevant.
GRC isn't just paperwork and checklists - it's about protecting our people and business from those who try to exploit trust. Think of it as building a human shield against social engineering attacks.
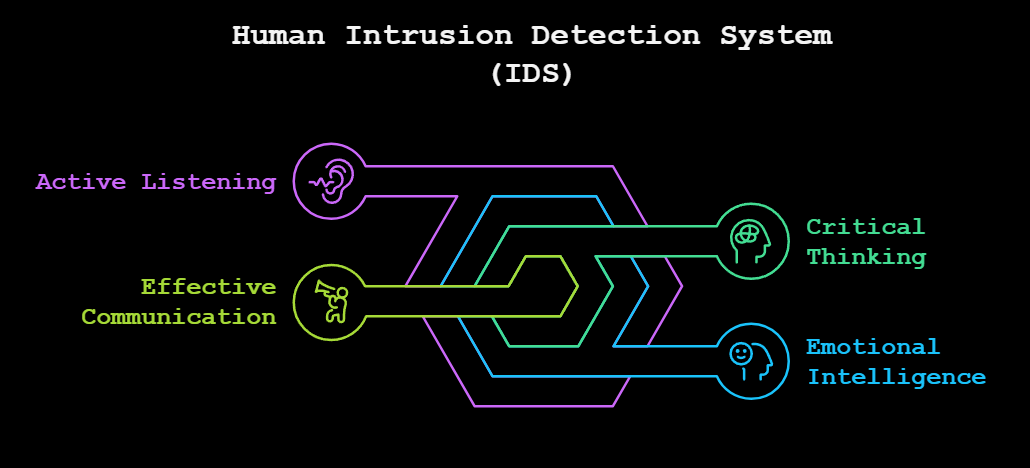
Soft Skills: The Ultimate Human IDS
To outsmart social engineers, you need a toolkit of soft skills sharper than any spear phish:
- Active Listening: Pay attention to what’s being said—and what’s not. Social engineers thrive on gaps in communication. The more you listen, the quicker you catch inconsistencies. [Read more on Active Listening.]
- Emotional Intelligence: Spot manipulation by understanding emotions (yours and others). Think of this as your personal social malware detector—because attackers don't just exploit technology, they exploit trust.
- Critical Thinking: Are your Spidey senses tingling? If something seems off or too good to be true, it probably is. Social engineers rely on knee-jerk reactions—critical thinking slows them down.
- Effective Communication: Encourage a culture of “if you see something, say something” without making employees feel uncomfortable. A workplace that talks about security is a workplace that builds resilience.
Level up these skills and you'll have a human IDS (Intrusion Detection System) that helps you dodge social exploits and keep your cool when things get sus.
Training Against Social Engineering
The best way to teach someone how to avoid a trap is to show them the trap—safely. Ethical social engineering techniques make training more interactive (and less of a corporate snoozefest):
- Simulated Phishing Campaigns: Train employees to spot and report suspicious emails.
- Pretexting Role-Play: Help teams identify manipulation tactics in real-time.
- Front Desk Defense: Run mock tailgating drills at secure entrances to reinforce access control.
- Gamify It: Make spotting scams a friendly competition. Who says security training can't be fun?
Foster curiosity and skepticism. Reward people for asking, "Wait, does this seem sketchy?" because a healthy dose of doubt is a social engineer's worst nightmare.
From Policy to Practice
Beyond training, align policies to support a strong security culture:
- Regular Training: Keep awareness fresh with consistent, evolving exercises.
- Clear Reporting Channels: Make it easy and judgment-free to report suspicious activity.
- Measure & Adapt: Track training results and adjust based on where employees struggle the most.
Social engineering isn’t going away, but neither is our ability to adapt and out smart the attackers.
Take Action Today
Whether you're a seasoned GRC professional or looking to make a career change to cybersecurity, defending against social engineering starts with you. Think of yourself as a human firewall - your awareness, instincts, and soft skills are your strongest defense against manipulation.
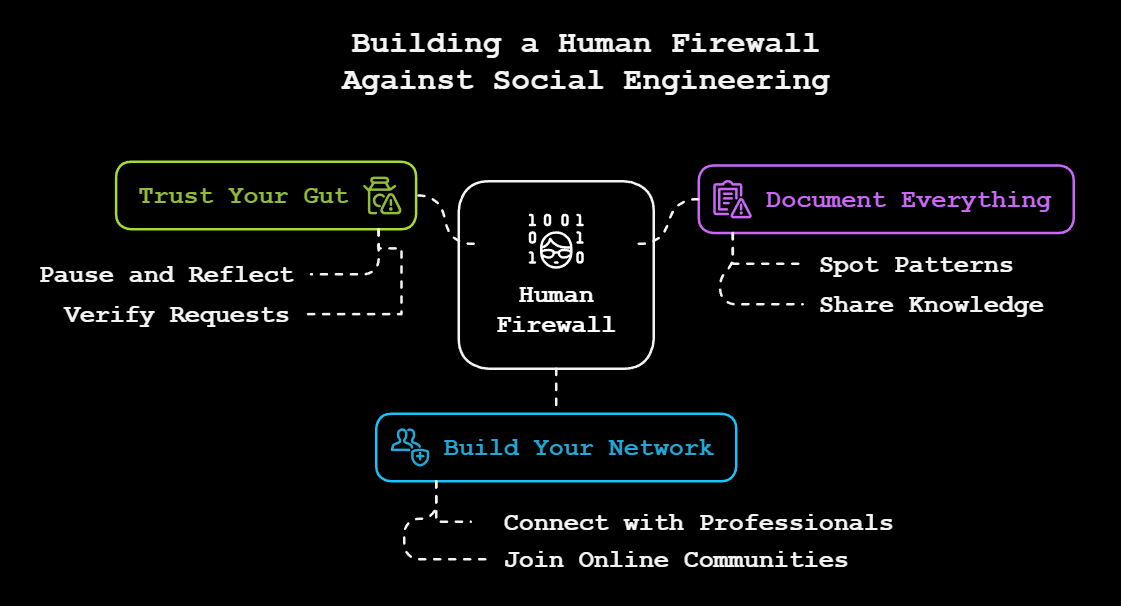
Ready to level up your social engineering defense? Start with these three simple steps:
- Trust Your Gut: If an email, call, or request feels off, pause and verify through official channels. Your instincts are often your first line of defense.
- Document Everything: Keep a log of suspicious interactions. What seemed odd? How did it make you feel? This helps you spot patterns and share knowledge with your team.
- Build Your Network: Connect with other security professionals, join online communities, and share experiences. A collaborative community sharing knowledge and experiences creates powerful protection against threats.