The Risk Register Playbook
The Risk Register Playbook: Think like a hacker, map your risks, and stay ahead of threats with a sharp, actionable risk register. Outsmart chaos before it starts.

When you hear “risk register,” you might picture endless spreadsheets or compliance checklists—boring enough to make even your printer nod off. Through a hacker's lens, it's a powerful cheat sheet for anticipating threats and planning defenses. Think of it as the ultimate weapon for staying two steps ahead.
Ready to start building your risk register? Let's dive in.
The Hacker’s Secret to Risk Management
Hackers anticipate weaknesses and act fast. A risk register empowers GRC pros to do the same—identifying, analyzing, and managing risks to dodge disasters. Hackers map vulnerabilities; you map risks. The difference? Your map stops chaos before it starts.
In today's world of AI-driven phishing and cloud security gaps, staying proactive isn't optional. A well-maintained risk register helps you spot threats before they disrupt your operations. It's not just defense; it's foresight.
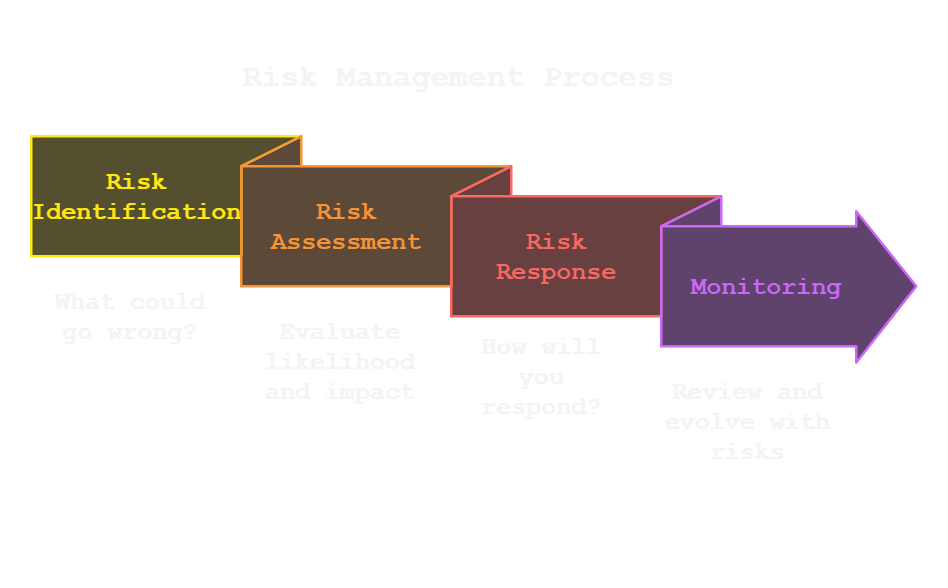
The Anatomy of a Risk Register
Risk Identification
This is your reconnaissance phase. What could go wrong? Cyber threats, compliance gaps, operational hiccups—document everything. Think like a hacker: What’s juicy enough to target? Where's the low-hanging fruit? Use tools like threat modeling, vulnerability scans, and tabletop sessions to uncover risks before they escalate.
Risk Assessment and Scoring
Evaluate risks based on two factors:
- Likelihood: What are the chances of this happening?
- Impact: How damaging would it be?
Scoring Methods:
- Qualitative Scoring: Quick high/medium/low rankings.
- Quantitative Scoring: Data-backed precision tied to a numeric or financial value, such as a 1-10 scale.
Risk Response Plans
Choose your strategy to respond:
- Mitigate: Reduce the risk (e.g., patch vulnerabilities).
- Avoid: Eliminate the risk (e.g., remove risky software).
- Transfer: Shift the risk elsewhere (e.g., insurance or third parties).
- Accept: Document and live with low-impact risks.
Get creative. Think like a hacker solving problems—only in reverse.
Monitoring and Reviewing Risks
Risks evolve. Regular reviews (quarterly or after major changes) keep your register relevant. Monitoring fosters a culture of proactive defense, something hackers hate.
Crafting a Risk Register That Works
Anticipate the Unthinkable
Start with the “what-ifs.” What could go wrong in a worst-case scenario? From supply chain disruptions to insider threats, map out these extremes and plan your defenses.
Prioritize High-Impact Risks
Focus on the risks most likely to derail operations or attract hackers’ attention. Think like an attacker: What vulnerabilities are easiest to exploit? Addressing high-impact risks first maximizes your resources.
Set SMART Goals
Vague goals don’t cut it in risk management. Replace them with Specific, Measurable, Achievable, Relevant, Time-bound (SMART) actions.
Collaborate Across Teams
Risks touch every corner of your organization. Involve IT, operations, finance, and even HR to gain diverse perspectives and uncover hidden vulnerabilities.
Refine and Update Often
Cyber threats evolve rapidly, from AI-powered attacks to zero-day exploits. Quarterly updates—or reviews after significant operational changes—ensure your register stays current and actionable.
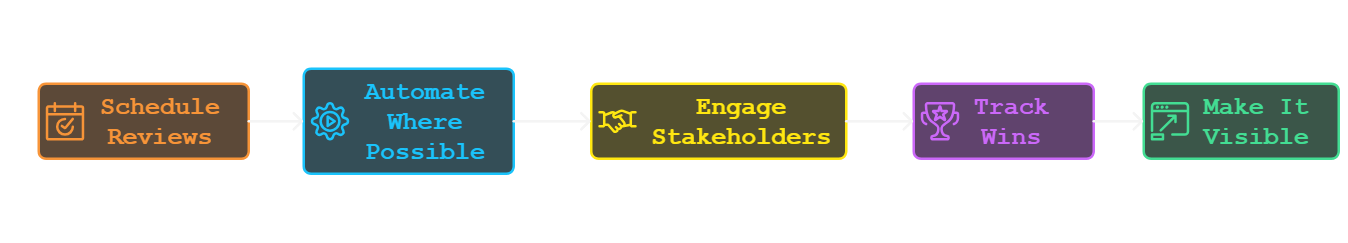
How to Keep Your Risk Register Alive
A risk register is only as valuable as the attention it gets. Without regular updates and engagement, even the best-built register loses its edge. Here's how to keep yours dynamic and effective:
- Schedule Reviews: Revisit your register quarterly or after operational changes. For example, assess whether new software introduces compliance gaps or security vulnerabilities.
- Automate Where Possible: Let tools flag outdated entries, track emerging threats, and streamline risk monitoring. Think of it as your risk register’s autopilot—just don’t fall asleep at the wheel.
- Engage Stakeholders: Collaborate across teams to reveal blind spots. Fresh eyes can often catch risks that others miss.
- Track Wins: Celebrate successes. Did your phishing simulation reduce click rates by 40%? Share these outcomes to foster a culture of proactive risk management.
- Make It Visible: Embed it into strategy meetings and dashboards to keep it actionable and top-of-mind. Use visualizations or dashboards to make your risk register an interactive part of executive briefings.
Risk Management in Action
Phishing remains one of the most common—and costly—cyber threats. Here's how a proactive risk register can turn risks into opportunities for measurable improvement:
- Mitigate: Implement multi-factor authentication (MFA) to reduce the likelihood of account compromise.
- Train: Conduct quarterly phishing simulations to educate employees. Gamify the experience with prizes for those who successfully identify phishing attempts.
- Monitor: Set up alerts for unusual logins, such as suspicious IPs or access times. Regularly review metrics like click rates and response times to refine your strategies.
Sample Risk Register
Winning With Risks
A risk register isn’t compliance busywork; it’s your playbook for staying ahead of threats. Build it with purpose, refine it often, and let it guide your proactive defense. Cyber threats evolve constantly, but with a sharp risk register, so will you.
