Why PCI DSS Isn't Enough
Think PCI DSS means security? Think again. This blog explores why compliance is just the start and offers strategies to build real, attacker-resistant security beyond the checklist.

Think being PCI DSS compliant means your organization is secure? Think again. That's like locking your front door while leaving the windows and back door wide open! Compliance is just the starting line—not the finish line for securing your organization.
Don't get me wrong, the PCI DSS has its place. It's a critical standard for protecting payment card data. But here's the catch: PCI DSS only covers the processes, people, and systems that interact with payment card data. The rest of your environment? Not in scope. And attackers know this.
Before we dive deeper, let's unpack what the PCI DSS is and why it's important.
PCI DSS 101: The Basics
The Payment Card Industry Data Security Standard (PCI DSS) is the payment card industry's way of setting ground rules for protecting payment data. Whether you're a global enterprise or the corner coffee shop, it applies to any organization that processes, stores, or transmits cardholder data. Think of it as the bare minimum—a foundation to build on, but not the full structure.
The standard, developed by the PCI Security Standards Council (PCI SSC), aims to reduce fraud, safeguard sensitive information, and ensure a baseline level of security for payment transactions.
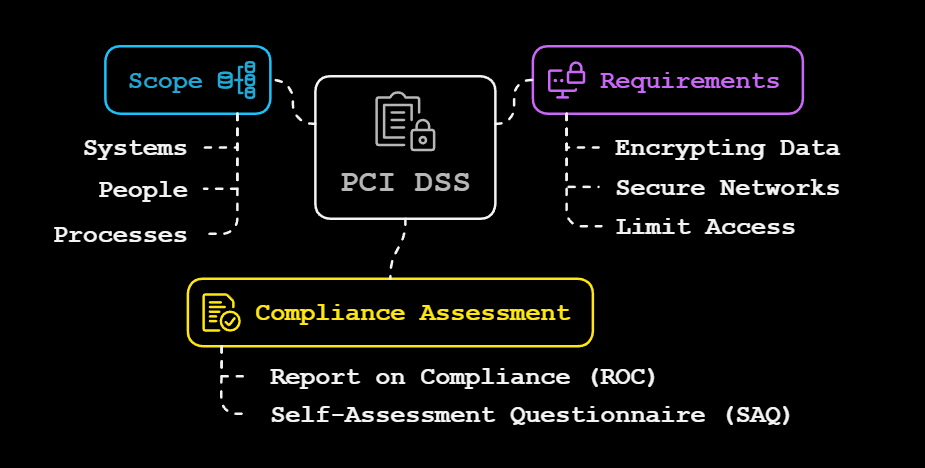
Key Components of PCI DSS:
- Scope: Applies only to systems, people, and processes that interact with payment card data. Everything else? Out of bounds.
- Requirements: There are 12 high-level requirements, like encrypting data, maintaining secure networks, and limiting access to sensitive systems—basic digital hygiene, really.
- Compliance Assessment: Entities validate PCI DSS compliance through either a Report on Compliance (ROC) or a Self-Assessment Questionnaire (SAQ), depending on eligibility and payment brand requirements.
The Gaps in PCI DSS
The PCI DSS provides a minimum standard—a way to prove to payment card companies that you're handling their data responsibly.
Think of the PCI DSS as securing one room in your house, while ignoring the rest. It's better than nothing, sure, but hackers aren't one-room kind of guests. They'll find the attic, the basement, or that shed you forgot existed. Threats like ransomware, insider attacks, and vulnerabilities outside your PCI systems? Not PCI DSS's problem.
This applies to other compliance standards as well. While some frameworks might cover the full environment, they're still only pieces of the puzzle. Compliance is not always security, and security is not always compliance. True security requires integrating multiple standards into a cohesive program and going beyond checklists and audits. Otherwise, organizations are left exposed to attackers who don't play by the rules.
The Scope of PCI DSS
The PCI DSS scope is tightly focused on the people, processes, and systems that interact with payment card data. To minimize risk, it's best practice to keep your PCI scope as small as possible.
How? Network segmentation. By isolating systems that handle cardholder data, you reduce the potential attack surface. Third-party processors like Stripe or Square can help by taking on some of the compliance burden. But transferring risk doesn't erase it. Vet your vendors like your data depends on it—because it does.
PCI DSS Isn't Bulletproof
Compliance alone won't keep attackers out. Here's why:
- Lateral Movement: Once inside your network, hackers don't stop at your PCI systems. They're like party crashers, searching for side doors or open windows. Without proper controls, they'll pivot their way to your crown jewels (sensitive data).
- False Sense of Security: A PCI DSS compliance logo might reassure leaders and consumers, but it's like a nightlight against the darkness of the threat landscape. Spoiler alert: The monsters are still there.
As security professionals, it's our responsibility to bridge this gap—educating stakeholders and advocating for a proactive, holistic approach to security.
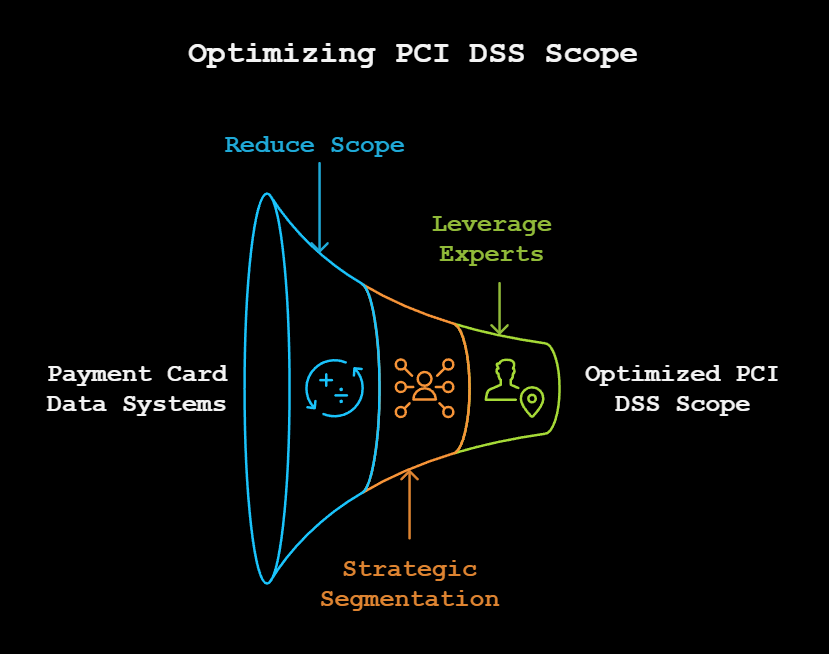
Optimizing Your PCI DSS Scope
Want to outsmart attackers? Start by managing your PCI DSS scope like a pro:
- Reduce Scope: Minimize the systems and processes handling payment card data.
- Strategic Segmentation: Segment networks to isolate PCI systems. Treat your network like a fortress, only trusted allies get near the treasure room.
- Leverage Experts: Bring in consultants to optimize your PCI DSS scope. Think of them as the Gandalf to your Frodo—they guide, but you still have to climb the mountain.
Moving Beyond Compliance
Compliance is the floor, not the ceiling. To build real security, organizations need a proactive, comprehensive strategy:
- Threat Modeling: Picture potential attack scenarios and secure your defenses.
- Incident Response: Rehearse plans for quick action during a suspected breach.
- Risk Assessments: Regularly evaluate risks across your entire environment, not just PCI systems.
To stay ahead of attackers:
- Conduct regular penetration testing to uncover vulnerabilities.
- Provide security awareness training to turn employees into your first line of defense.
- Deploy robust endpoint protections to stop breaches before they start.
Think of security as a chess game. Stay several moves ahead, anticipate your opponent's strategies, and protect your queen (sensitive data) at all costs.
The Consumer Perspective
See a PCI DSS compliance logo? It doesn't mean your data is invincible.
Consumers should be asking:
- "What else is this company doing to protect my data?"
- Is there encryption?
- Do they use multi-factor authentication (MFA)?
Transparency about security practices builds trust and shows a commitment to more than just compliance, keeping businesses accountable.
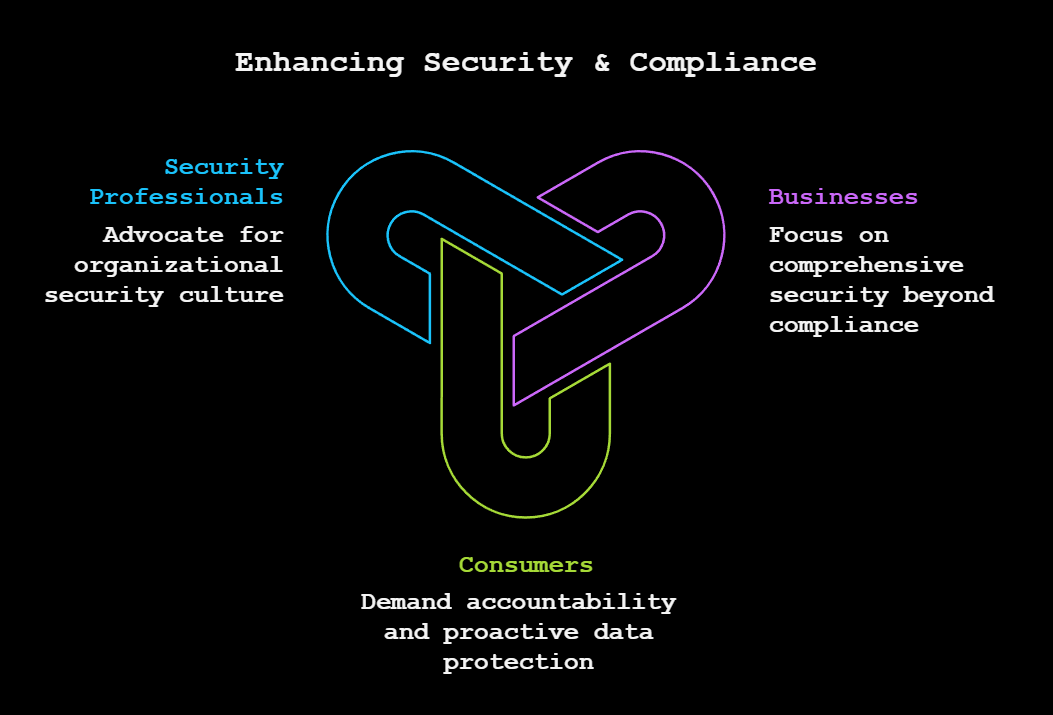
Key Takeaways
For Businesses
Think beyond compliance checklists. Locking one door (PCI DSS compliance) is a start, but real security means guarding every entry point. Build a culture of transparency and continuous improvement—it's good for your consumers and your bottom line.
For Consumers
Don't settle for a compliance logo. Demand more. Ask questions, do your research, and prioritize companies that show a commitment to protecting your data.
For Security Professionals
Be the advocate your organization needs. Educate, collaborate, and lead the charge to make security everyone's responsibility—not just a compliance checkbox.
Hacking Compliance: Pro Tips
- Critical Thinking: Treat compliance as a baseline, not a destination.
- Creativity: Use innovative solutions to enhance security.
- Confidence: Advocate for necessary security measures, even when budgets are tight.
